The crypto world is reeling from an unprecedented Bybit Hack. The infamous Lazarus Group, a state-backed North Korean hacking collective, has executed the largest crypto theft in history, siphoning a staggering $1.46 billion from the Bybit exchange. But this wasn’t a sophisticated code exploit; it was a calculated manipulation of people.

Lazarus Strikes Again: A History of High-Stakes Theft
Lazarus has a notorious track record, having stolen billions from banks, crypto exchanges, and DeFi protocols. Their latest target, Bybit, fell victim to a strategy that bypassed traditional security measures.
The Human Element: How Bybit’s Multisig Security Was Compromised
Unlike typical crypto hacks, this attack didn’t involve breached code or leaked private keys. Instead, Lazarus exploited the human element of Bybit’s multisig security. Bybit’s own multisig signers, believing they were authorizing a routine transfer, unknowingly approved transactions that emptied their entire cold wallet.
A Terrifying Question: How Did Lazarus Identify Their Targets?
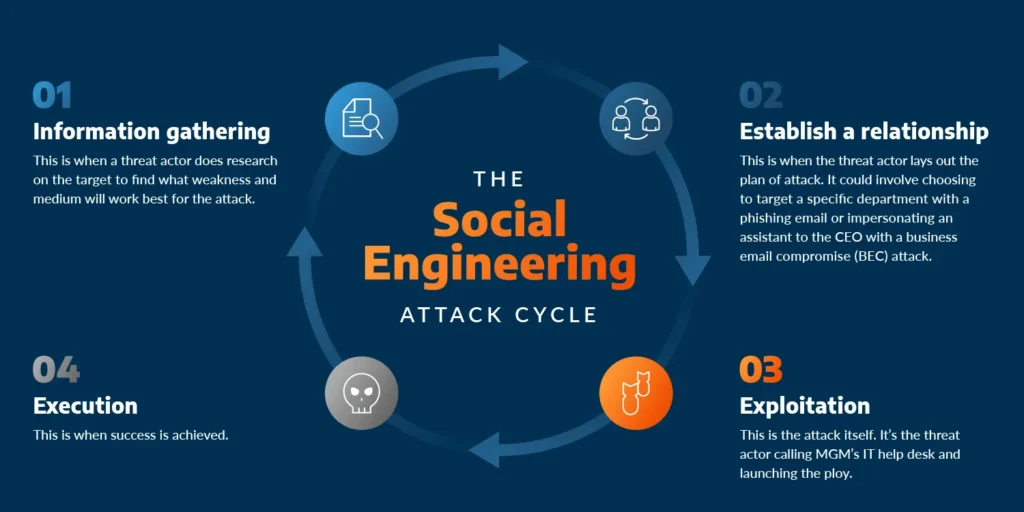
The success of this attack hinges on Lazarus’s ability to identify and manipulate specific individuals. A multisig wallet requires multiple signers, and even a single refusal would have thwarted the Bybit Hack. This raises critical questions:
- Inside Job? Was there an insider who leaked the signer list?
- Social Engineering? Did Lazarus meticulously study emails and behaviors to identify vulnerabilities?
- Device Compromise? Were the signers’ devices infected with malware?
These possibilities highlight the vulnerability of even the most secure systems to human error and manipulation.
The Scale of the Theft: Lazarus’s Massive Ethereum Holdings
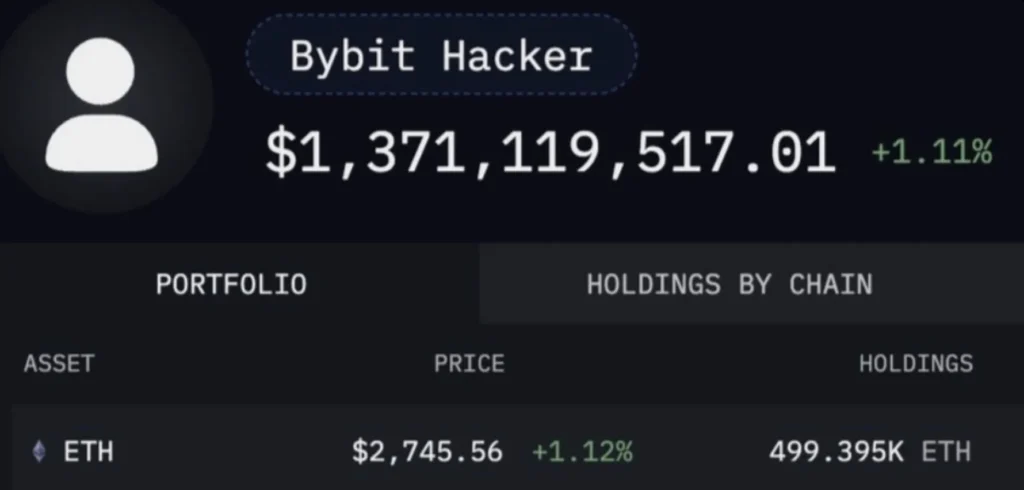
The sheer scale of the theft is staggering. Lazarus now controls 0.42% of all Ethereum in circulation, surpassing the holdings of the Ethereum Foundation, Vitalik Buterin, and major institutions like Fidelity.
Laundering the Loot: Lazarus’s Proven Tactics
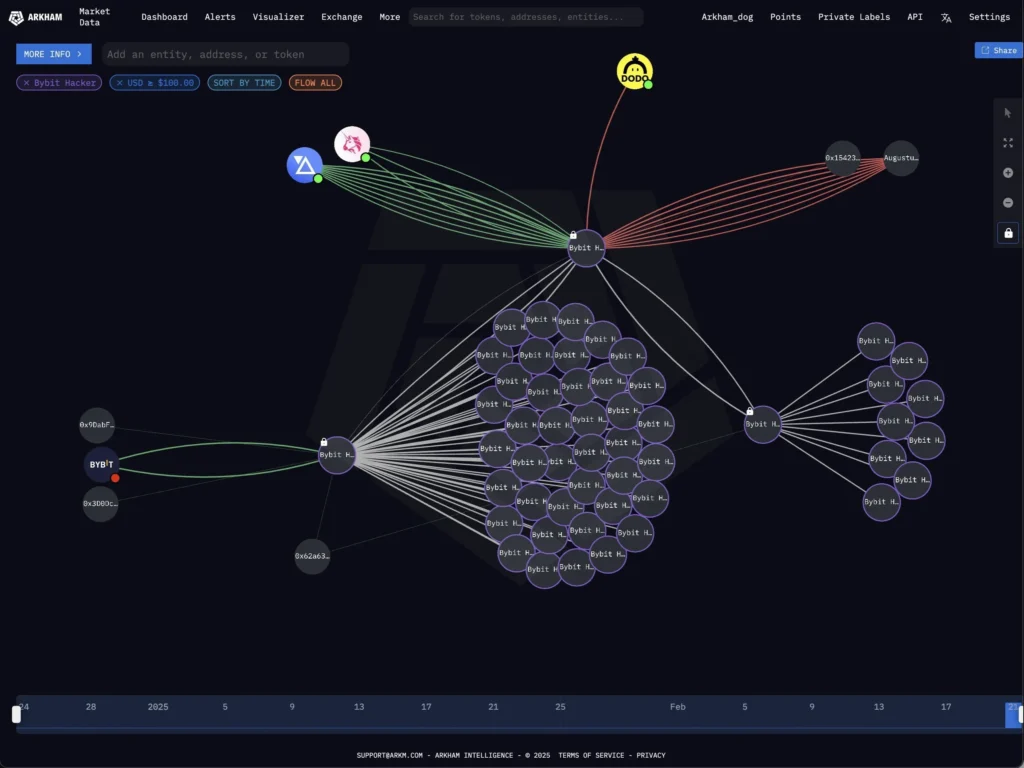
Moving such a massive amount of Ethereum without detection is a monumental challenge. Lazarus has a history of employing various laundering techniques, including:
- Bridging to other blockchains
- Utilizing on-chain mixing services
- Engaging in OTC trading through illicit brokers
Investigators have already flagged the 53 wallets holding the stolen ETH, making immediate cash-outs or swaps highly risky. However, Lazarus is known for its patience.
The Waiting Game: Lazarus’s Long-Term Strategy
Chainalysis reports that Lazarus still holds $55 million from hacks dating back to 2016. They are not known for quick cash-outs; they prefer to wait, making recovery efforts exceedingly difficult. Notably, no one has ever successfully recovered funds stolen by Lazarus. They do not negotiate or return funds.
Bybit’s Response: Assurances and Liquidity
In response to the crisis, Bybit’s CEO, Ben Zhou, has publicly addressed the situation, assuring users that:
- Client funds are 1:1 backed.
- The exchange has sufficient liquidity to cover withdrawals.
- All other wallets remain secure.
So far, these assurances have prevented a bank run.
The Unsettling Reality: No One Is Truly Safe
The Bybit Hack serves as a stark reminder that even the most advanced security measures can be compromised by human vulnerabilities. This incident underscores the need for heightened vigilance and robust security protocols across the entire crypto industry.

Leave a Reply